You heard it right, “Zero Trust”. Unlike human being who can innately identify stranger from friend and appropriately facilitate trust, network infrastructure is incapable of distinguishing friend from foe. It requires well planned initiatives, tools and mechanisms to enable anomaly detection capability in a network infrastructure.
In traditional deployment, an innate trust is applied to users of intranet while increase scrutiny reserved for external traffic. Such concept is fundamentally flawed. In many cases, attacks are originating internally from malware plagued user endpoints than directly from outside. Lockheed martin Cyber Kill Chain® framework explains this phenomenon very well. The framework identifies 7 steps adversaries take to achieve their objective in cyber intrusion.
Figure 1. Lockheed Martin Cyber Kill Chain® Depicting how hacker gain access to network resources (Lockheed Martin, 2019)
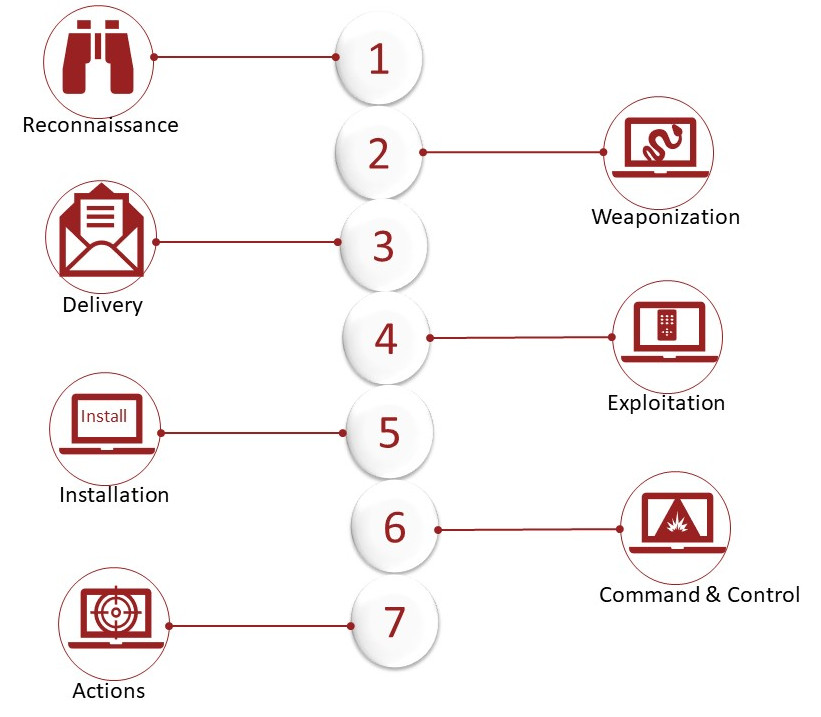
Collectively these 7 steps comprise of APT (Advanced Persistent Threats) technique that hackers use to gain access to network resources and stay undetected for a period of time:
- Reconnaissance: This is first step in hacking which involves information gathering about people, host and network. Hacker may scan press release, internet, social networks and other media to learn about people of a targeted organization, next step is discovering possible victim (s). Hacker may use tool such as nmap and ping scan etc to gain an understanding of networks and hosts involved.
- Weaponization: In this phase, hacker uses information gathered previously to prepare for attack It may involve creating believable Spear Phishing e-mails which is look alike of e-mails that can be potentially received from a known vendor or other business contact. Victim may be then directed to a fake web page identical to vendor’s website through a technique called “Watering Holes”. The sole purpose is to capture your username and password, or to offer you a free download of a document or something else of interest. The process will help hacker gain required credential gain access to the network in order to successfully exploit any vulnerabilities that they may find.
- Delivery: Now, hacker starts the attack that may include a series or things e.g. Phishing e-mails with weaponized attachment or redirection to fake web page where user credential is collected. If the Phishing e-mail contains a malware as attachment, then attacker waits for someone to open the attachment and for the malware to call back.
- Exploitation: In this phase, hacker uses victim’s credential e.g. username and password to access the network. If victim opened the malware laced attachment, then hacker remotely accesses to computer.
- Installation: In order to keep sustain access in the network, hacker install code for backdoor access, possibly launch attack to other computers and may create admin accounts and turn off firewall rules etc.
- Command & Control: Now, hacker may have access of other computers, an understanding of network and even better credentials to gain uninterrupted access to data and applications. At this point hacker is in control of network infrastructure.
- Action on Objectives: With control of network, hacker now have upper hand to achieve their objectives. They could be stealing product design, user data and other confidential information to either monetize the data or use it to cause harm to targeted organization.
As evident from the steps of APT (Advance Persistent Threat), hacker may use a computer of an internal user to launch attack to the network. Same can be done through network devices and Wi-Fi or IOT gateways. According to ZDNET, thousands of Wi-Fi gateway including Huawei HG532 and Realtek RTL81XX were exploited by Gafgyt malware that takes advantage of known vulnerabilities to rope these devices into a botnet for the purpose of setting Distributed Denial of Service (DDOS) attack (ZDNET, 2019). This brings us to the very question of “Trust” for devices and users that are inside or outside of network perimeter and trying to connect to network.
Read about "zero trust" at https://innovaxtech.com/index.php/en/blog-list/zero-trust-networks/practical-approach-to-zero-trust

Comments